Introduction
In the fast-evolving world of digital technology, cybersecurity threats have also advanced, becoming increasingly sophisticated and difficult to manage. As organizations move towards greater online presence, cloud storage, and interconnected systems, they face a rise in malicious attacks, ranging from ransomware and phishing to zero-day exploits. Sandboxing, a technique that isolates applications or files in a controlled environment, has become a vital strategy in the battle to prevent cyber attacks. By examining what sandboxing is, its benefits, and its role in cybersecurity, organizations can better understand how this technology strengthens their defense mechanisms.
Definition
Sandboxing is a cybersecurity technique that isolates potentially malicious files, applications, or code in a controlled, virtual environment to test their behavior without risking harm to the main system. By running these files in a secure “sandbox,” security professionals can observe how they behave, such as whether they attempt to access sensitive data or alter system settings. This approach helps detect threats like malware or zero-day vulnerabilities without exposing the actual network or device to potential damage, making sandboxing an essential tool for identifying and containing cyber threats before they reach production environments.
What Is Sandboxing?
Sandboxing is a cybersecurity practice designed to test and analyze untrusted files or applications within a secure, isolated environment known as a “sandbox.” This “sandbox” simulates an operating environment, allowing the user to observe the behavior of a potentially malicious program without risking harm to the rest of the network or system. By executing files or code in a sandbox, analysts can inspect the file’s behavior, evaluate any malicious activities, and determine whether it is safe to deploy. This way, any malicious actions can be contained and prevented from affecting the larger system.
How Sandboxing Works
Sandboxing relies on isolating a program or file so it can be examined in a separate environment, often referred to as a virtual machine (VM) or container. The process involves several steps, including:
Setup of the Sandbox Environment: A virtual replica of the operating environment is created, mimicking the network, software, and configuration of the original system. This replication ensures the isolated environment accurately reflects real-world conditions, helping to capture any malware behavior accurately.
File or Application Execution: The suspicious file, link, or program is executed within the sandbox, simulating real-world usage to observe its behavior. During this phase, any attempts to access files, make unauthorized changes, or communicate with external servers are closely monitored.
Behavioral Analysis: Security software analyzes the behavior of the isolated file or program, noting any suspicious activities. Behavioral analysis is vital because many modern malware programs attempt to hide from detection tools. This step includes watching for changes to system settings, registry access, attempts to communicate with command and control servers, and other indicators of compromise.
Reporting and Action: If the program displays malicious behaviors, sandboxing software can alert security teams and automatically isolate the threat. Based on findings, security analysts decide whether to block, quarantine, or delete the malicious file. If deemed safe, the program can then be deployed in the production environment.
Sandboxing methods vary depending on the software used, but most systems aim to simulate realistic environments to reveal any hidden malware. Advanced sandboxing tools can even mimic a specific operating system or hardware setup, giving analysts a highly tailored environment for their evaluations.
Key Benefits of Sandboxing in Cybersecurity
Sandboxing has become indispensable for cybersecurity due to its robust threat detection and prevention capabilities. Some of the most significant benefits include:
Protection Against Zero-Day Threats: Zero-day vulnerabilities are unknown weaknesses in software that attackers can exploit before developers patch them. Traditional security tools often fail to detect these attacks, but sandboxing can reveal these threats by capturing the abnormal behavior of applications or files in a safe environment.
Improved Malware Detection: Unlike traditional antivirus software that relies on signatures, sandboxing performs behavioral analysis, making it effective against previously unseen threats. By examining files for malicious behavior, sandboxing enables organizations to detect malware even when it isn’t recognizable by standard antivirus databases.
Enhanced Threat Intelligence: By analyzing the behavior of malicious files, organizations gain valuable insights into new attack techniques and malware strains. This intelligence aids in developing targeted defenses, refining threat detection tools, and understanding potential vulnerabilities.
Reduced False Positives: Many cybersecurity tools can mistakenly flag safe files or applications as malicious, which can be disruptive and costly. Sandboxing reduces false positives by accurately examining the file’s behavior, allowing security analysts to focus on genuine threats.
Minimal Business Disruption: Sandboxing minimizes the risk of disruptions in day-to-day operations by detecting and containing threats before they reach the production environment. This proactive approach helps maintain business continuity and protects users from potential breaches.
Cost-Effective Cyber Defense: Dealing with a successful cyber attack can be financially draining, not to mention the potential reputational damage. Sandboxing provides an additional layer of security that helps prevent attacks from spreading throughout the network, making it a cost-effective solution for cybersecurity.
Sandboxing in Different Cybersecurity Contexts
Sandboxing is versatile and finds use across multiple sectors of cybersecurity, providing tailored solutions for various applications:
Network Security: In network security, sandboxing inspects data packets or emails before they reach end-users. By isolating incoming files and attachments in a sandbox, network administrators can prevent malware from infecting systems through phishing emails or other common attack vectors.
Web Security: Web browsers often use sandboxing to limit the access of individual web pages to the overall system. This isolation helps protect users from malicious websites that attempt to install malware, mine data, or conduct other malicious actions.
Endpoint Security: Endpoint security solutions often incorporate sandboxing to analyze files before they are executed on local machines. This approach prevents malware from infecting endpoints like desktops, laptops, and mobile devices by containing threats before they spread.
Application Security: In application development, sandboxing plays an important role in ensuring that newly developed software does not contain vulnerabilities. Developers can test applications in sandboxed environments to identify weaknesses or potential security issues before deployment.
Challenges and Limitations of Sandboxing
While sandboxing is highly effective, it’s not without its challenges:
Resource-Intensive: Virtual machines or container-based sandboxes require significant computing resources, which may slow down system performance.
Evasion Techniques: Sophisticated malware can sometimes detect when it’s in a sandbox environment and modify its behavior to avoid detection. This can make it challenging for sandboxing solutions to catch all threats.
Complexity of Setup and Maintenance: Implementing and maintaining a sandboxing environment requires technical expertise and continuous monitoring, which can increase operational costs.
False Positives: Sandboxing may sometimes misclassify benign applications as suspicious, causing unnecessary disruptions.
Future of Sandboxing in Cybersecurity
As cybersecurity threats continue to grow in complexity, sandboxing technology will evolve to meet these new challenges. Artificial intelligence (AI) and machine learning (ML) are already being integrated into sandboxing solutions to enhance threat detection and predictive analysis. AI can help identify anomalies faster and adapt to new types of malware, while machine learning can improve the detection rate by learning from previous threat patterns.
The demand for cloud-based sandboxing solutions is also increasing, especially with the rise of remote work and cloud-based applications. Cloud-based sandboxing offers scalability and reduces infrastructure costs, making it an appealing option for businesses of all sizes. Additionally, cloud sandboxes can be updated in real time, ensuring that they remain effective against the latest cyber threats.
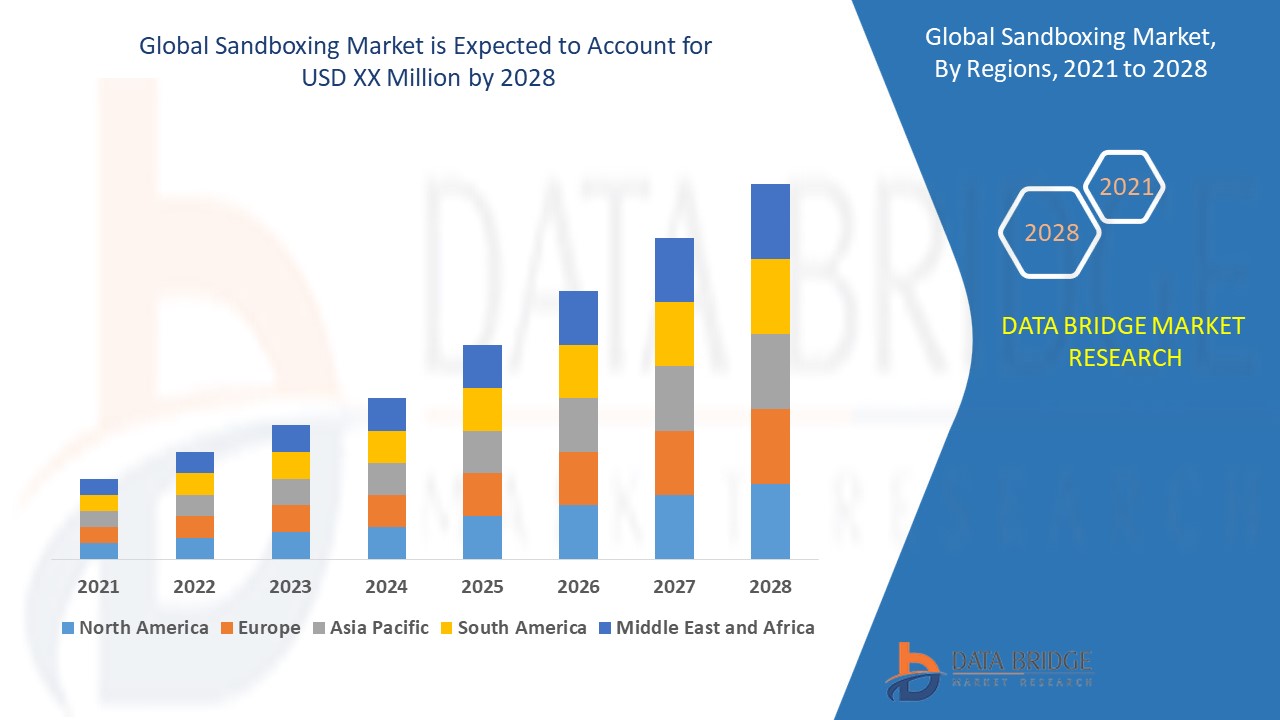
Growth Rate of Sandboxing Market
It is expected that the sandboxing market would expand at a rate of 19.55% between 2021 and 2028. This research from Data Bridge Market Research on the sandboxing market offers insights and analysis on the several elements that are anticipated to be prevalent throughout the course of the forecast period, along with their effects on the market’s growth.
Read More: https://www.databridgemarketresearch.com/reports/global-sandboxing-market
Conclusion
Sandboxing is an essential cybersecurity tool that helps protect organizations from sophisticated and unknown threats. By isolating suspicious files or applications, sandboxing enables security teams to detect and mitigate malware, zero-day vulnerabilities, and other risks without endangering the main network. Although it has limitations, such as resource demands and the potential for sandbox evasion, the benefits of sandboxing far outweigh these drawbacks when used alongside other cybersecurity measures.